This year, people attending ISTE in person received an email with instructions about how to provide proof of vaccination status or proof of a negative Covid test.
While the goals of ISTE’s efforts are laudable (reduce the chance of ISTE becoming a superspreader event), their implementation demonstrates how getting privacy right requires thought and planning. The fact that one of the major EdTech conferences in the world missed some basic details on getting privacy right should lead to some thought about why data privacy isn’t better in K12 schools in general.
This post details preliminary findings; I will detail my process throughout so anyone can verify or replicate what I describe here. This post is a quick and shallow look at the issues; a more detailed review would almost certainly find additional issues and add additional nuance.
The email ISTE sent to some (possibly all) attendees is shown below, with identifying information about the recipient omitted.
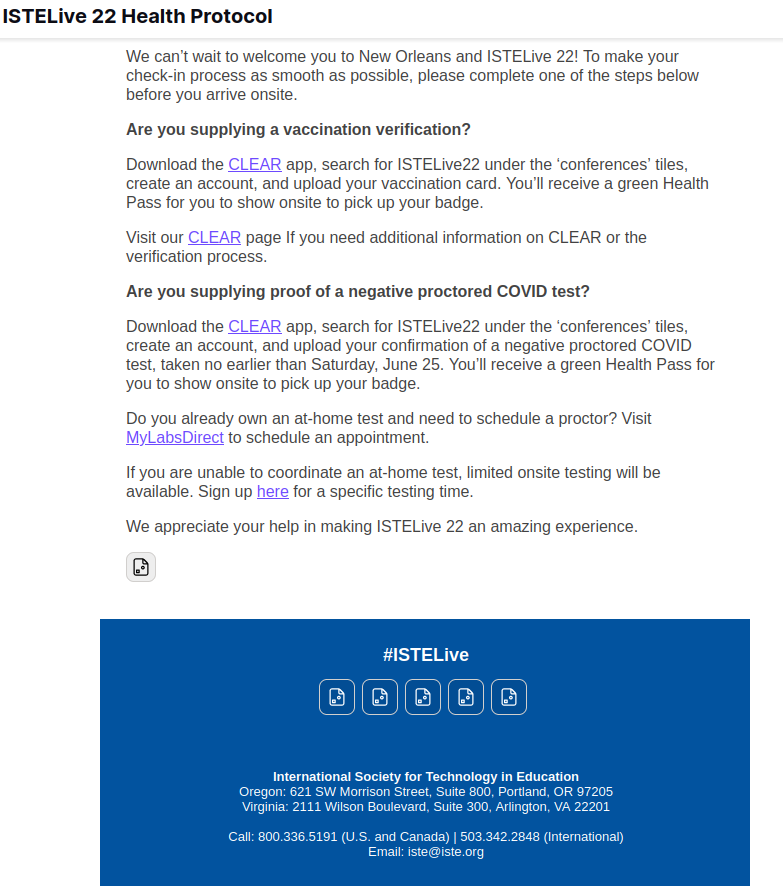
This email is the gateway to three problems that will be described in this post.
The Problems
Problem 1: Links in the ISTE email are mangled to include tracking code, and this tracking leaks the recipient’s email addresses.
Every link in the email sent by ISTE has been mangled to contain tracking code, and these tracking links are both unencrypted and contain the recipient’s email address. This means that every time a person clicks on a link from the email shown above, their action is visible to anyone who can view traffic on the network.
To see this problem in action, right click on a link in the email, and save the link to your clipboard.
Then, head on over to Cyberchef, and paste the link into their input field, and use the Base64 decoding feature. The decoded link will reveal the actual url you want to visit, with your email at the end. In the screenshot below, I redacted the email address to protect the privacy of the recipient.
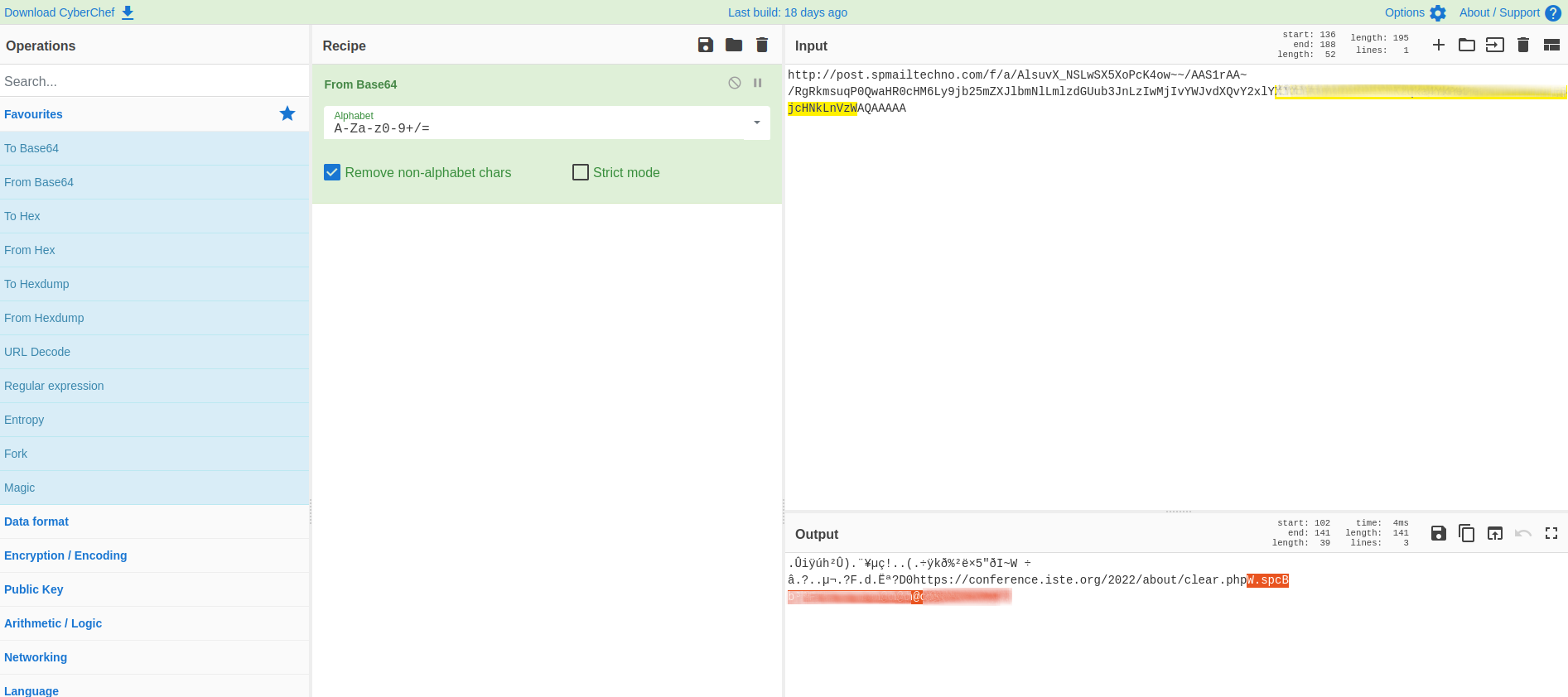
Note also that the mangled URL from ISTE is unencrypted (it starts with “http” not “https”).
Problem 2: People are required to use the CLEAR mobile app, and a static analysis of the mobile app suggests that the app uses third party data companies for tracking.
Static analysis looks at the codebase of an application, and runs automated tests against that codebase. Static analysis is a useful tool for highlighting areas of additional research.
The static analysis of the Clear app shows trackers from multiple data collection companies (from adtech to analytics) used in the app.
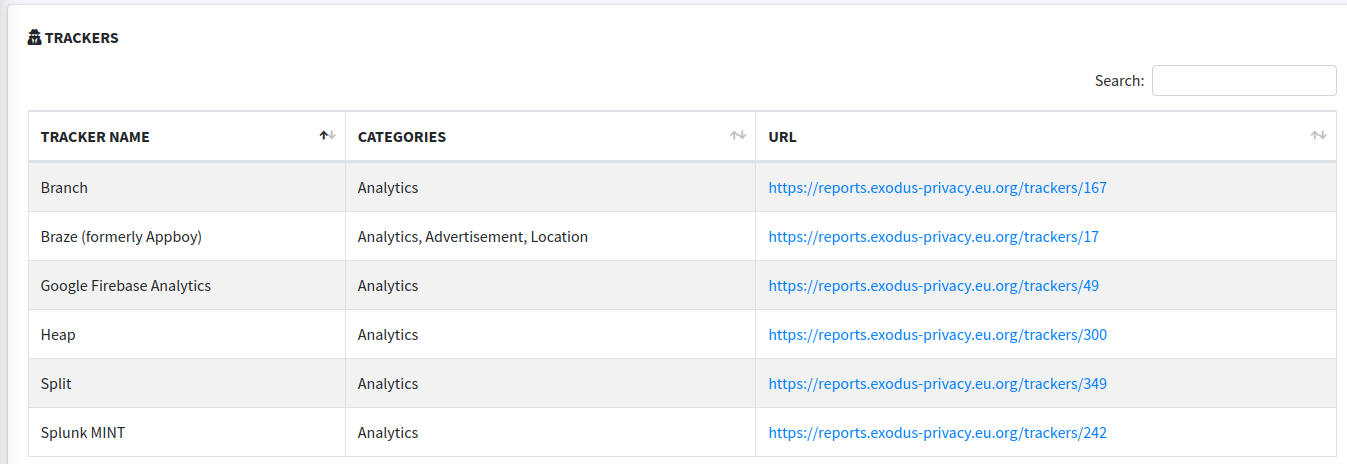
The range of data collected and retained by these services is not clear from the static analysis, but Braze in particular has a well documented ability to collect and retain precise profiles about people. The ISTE email does not make any mention of conference attendees sharing data with Braze, or any of these other third parties.
Static analysis was run on June 27th, using MobSF version 3.5.2 Beta.
Problem 3: the CLEAR privacy policy linked from the app page implies that Clear engages in broad data collection about users, and can share some data with third party adtech companies.
Clear’s privacy policy states that they can get information about people from various sources, including the Clear app. This implies that Clear augments data about users with data they get from other third party sources. The exact language in their policy is:
“We may obtain personal information about you from various sources, including the CLEAR membership application.”
The practice of collecting data about people from third parties is called data augmentation. It’s how companies build data profiles about their users, often without clear notice or consent.
The privacy policy also states that visitors to “our website” will have data collected about them that are used in advertising.
“We collect data about your visit to our website to provide advertising about products and services tailored to your individual interests. Therefore, you may see certain ads on other websites because we participate in advertising networks run by third-party vendors. Those networks track your online activities through automated means, including the use of cookies and web beacons. The networks use this information to show advertisements tailored to your interests. Our ad network vendors receive information about your visit to our website, such as the pages you have viewed. This information also helps us track the effectiveness of our marketing efforts.”
The presence of third party ad trackers observed via static analysis in the android app suggests that Clear also could be collecting ad-related data about users via the mobile app, and sharing that data with third party adtech companies.
Conclusion
ISTE is requiring people to use the CLEAR app. This means that ISTE is driving tens of thousands of new users into Clear’s data collection ecosystem. In an ideal world, an organization dedicated to educational technology would have a greater awareness and level of attention about basic privacy, and would be more proactive in protecting the privacy of their conference attendees.
