On March 22, on Twitter, @bubbaprog posted about receiving a phishing email that targeted verified Twitter users.
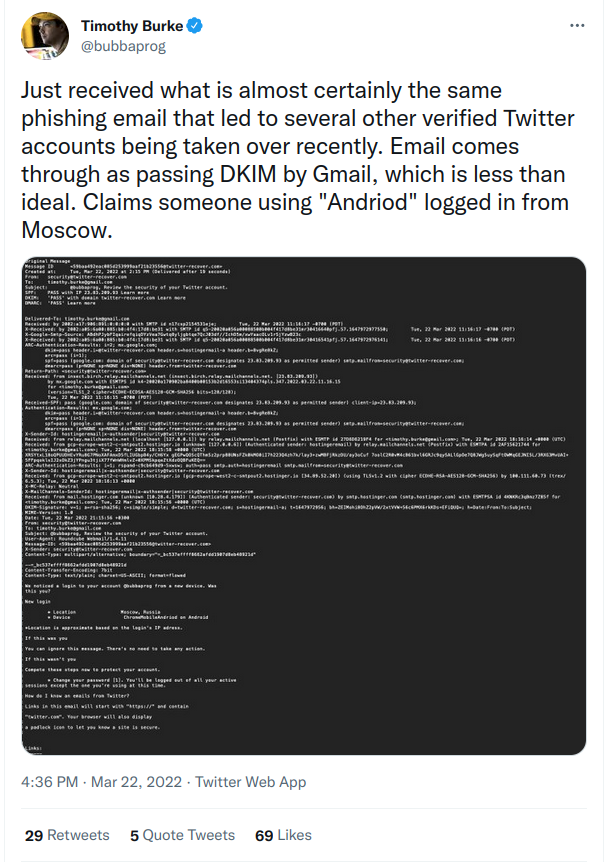
The thing that made this post stand out to me was the observation that the email passed Gmail’s DKIM check. DKIM is part of a suite of settings — along with SPF and DMARC — that domain owners can set to validate that a specific email is being sent legitimately from a specific domain. If a message passes DMARC validation checks, that’s generally interpreted as an indication of reliability.
Unfortunately, anyone who controls a domain can set up DKIM, SPF, and DMARC. So a bad actor with a domain that appears legitimate can manipulate the tools that “protect” against spam to phish, spread ransomware, spread malware, and engage in other types of fraud and theft more effectively.
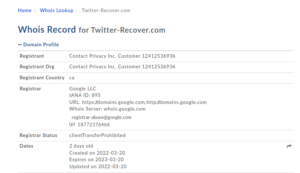
A check of the WHOIS record showed that the domain in question — twitter-recover.com had been registered for two days when the email was sent. The people who bought the fraudulent domain set up DKIM, SPF, and DMARC.
This is why we can’t have nice things.
1. Introduction
During the pandemic, ransomware and malware attacks have, by most counts, been steadily increasing, and schools are popular targets.
In this post, I’m going to focus on an element used in launching online attacks: typosquatting. Typosquatting isn’t new, by any stretch, but it’s a central piece of successful attacks that often goes overlooked. This post covers the basics of how typosquatting can be used in an attack, and how to mitigate the risk of these attacks. To demonstrate the risk, in addition to the example from Twitter, two more concrete examples from well known companies will highlight how typosquatting can be used as part of phishing, spearphishing, ransomware, malware, keyloggers, and other forms of online malfeasance. These concrete examples will help illustrate how nearly the entire edtech industry needs to do more to prevent typosquatting, and to spread awareness about how to avoid attacks that incorporate typosquatting.
Successful online attacks are more likely to succeed when targets are rushed, stressed, or pressured. Any factors that short circuit skepticism, caution, or critical analysis help a potential attacker. In the United States, at the time that I am writing this post, school staff, teachers, parents, and students are navigating the third academic year of the pandemic. In many cases, notifications from schools, health systems, and employers will be sent from platforms with unfamiliar names. It’s an ideal time for people to use typosquatted domains in attacks.
NOTE: Nothing in this post is new, and all of the information in this post is well known to criminals engaged in online crime. The information in this post is also known to the companies that have the ability to help protect us from online crime – in some cases, I have spoken with people at these companies personally, or worked to ensure that people at these companies were made aware of the risks. The people who know the least about this (in general terms) are regular folks who are most likely to be targeted by criminals.
2. Typosquatting 101
Typosquatting can be used in a range of ways, from ad fraud, to phishing a person’s login credentials or other personal information, to delivering ransomware or keylogging software designed to harvest more personal information, to delivering malware as part of a larger, coordinated attack. None of these attacks lead to anything good for end users.
Unfortunately, typosquatting is ridiculously simple to do (and in this post, when I say “typosquatting” I am including similar attacks such as adding a word to create a plausible sounding domain name). Typosquatting is different than email spoofing, where a malicious actor can forge the sender addresses to make the email appear to be from a trusted source. While both email spoofing and typosquatting are a form of deceit that tries to trick a target into believing that they are communicating with a trusted source, typosquatting has a significant advantage to an attacker: the attacker owns the domain, and can use that as part of the attack.
For this post, I will use examples from two well known companies with domain names I have purchased. To be clear: I have no desire to use these domains; I have no desire to own these domains, and I will gladly transfer them to their respective companies. The fact that I was able to buy them in August 2021 is more than a little ridiculous and unsafe.
And a note on these domains: I found them with minimal effort, with under 10 minutes of searching. I bought the domains because I can’t in good conscience write about this subject and leave potential sources of attack available. But, after buying seven domains, and spending a little over $100 (approximately 15/domain), I stopped looking. To repeat: these domains should not be available. The fact that they are available in August 2021 highlights the negligence of companies in taking basic steps.
Nothing that I am saying in this post is news to law enforcement, or cybercriminals, or even the companies themselves. The MITRE ATT&CK site (and be sure to follow them on Twitter ) has a page dedicated to typosquatting , and a page documenting how attackers obtain online infrastructure to use in their attacks. The FBI and the Cybersecurity and Infrastructure Security Agency documented how typosquatting was a central part of Chinese cyberattacks in July 2021. Typosquatting is not new, and the MITRE ATT&CK site lays out the core mitigation pretty clearly: “Organizations may intentionally register similar domains to their own to deter adversaries from creating typosquatting domains.”
3. Examples
The example from Twitter, shown in the beginning of this post, shows how domains that appear legitimate can be used to support fraud. But Twitter has plenty of company — both Google and Apple are susceptible to having their brand used in typosquatting attacks.
3A. Google
In 1998, Google was one of the earlier sites to be affected by typosquatting when someone acquired the site goggle (dot) com. Don’t visit this domain; it has been used to serve malware in the past.
And, one would think that, because Google is Google and because Google has a long history with typosquatting that they would have this buttoned up, but they don’t. Remember: for an attack to be successful, it only needs to succeed once. In mid-August, I was able to purchase http://g00q1e.com/ – an ugly lookalike for Google with “0” swapped for “o”, and “q” swapped for the second “g”. A domain like this could be used behind a legitimate looking link to (DON’T CLICK – MOUSE OVER TO SEE THE LINK) Google.com but it could then push someone to the typosquatted domain.
And if you think it’s hard to clone a domain, I have some bad news for you. There are myriad ways to clone and replicate domains. But the short version: it takes under two minutes to clone an exact copy of a page in a domain.
Criminals know how to clone sites, and how to host those cloned sites using junk domains.
Which raises the question: Google has no shortage of resources – why aren’t they buying domains like this more aggressively? Or: why are junk domains, and obviously fraudulent domains like twitter-recover.com, on the market?
3B. Apple
In early August 2021, Apple announced that it would scan images on iPhones looking for matches against a known set of child sexual abuse material (CSAM). While Apple delayed the rollout due to pushback from a broad range of the sentient world, Apple’s proposed plan included notifications to parents. Prior to the rollout, Apple said on it’s child safety page(this is a link to an archived version of the page from the time of the announcement – the current version does not have these statements), “the child can also be told that, to make sure they are safe, their parents will get a message if they do view it (an image Apple has identified as being sexually explicit or CSAM).” This scanning occurs on phones, and users do not have any choice about whether or not the content of their phones are scanned (aside from not using Apple products).
Apple also stated that the scanning can trigger notification to law enforcement: “This innovative new technology allows Apple to provide valuable and actionable information to NCMEC and law enforcement regarding the proliferation of known CSAM.”
NOTE: Both of these claims are no longer on the current Child Safety page.
This post is not about about the privacy and security implications of this technology; there is already plenty of discussion about the issues with Apple’s approach and how it could be weaponized or modified to support authoritarian regimes. And to state the obvious, CSAM is a scourge and people who traffic in it are scum who deserve no quarter.
However, Apple’s deployment of this feature created an obvious attack vector for criminals: the notification of false positives. Shortly after Apple’s announcement in mid-August of 2021, I was able to purchase six relevant domains:
- imagescan-apple.com
- alerts-apple.com
- images-apple.com
- ncmec-apple.com
- csam-apple.com
- children-apple.com
Finding these domains took under two minutes; purchasing them took under 5 minutes, and cost $90.00 US. To repeat myself for emphasis: I do not want these domains. It makes me uncomfortable looking at them, and they need to never be used. I will happily hand them over to Apple or any other responsible entity that safeguards junk domains and ensures they domains will never be used. But Apple announced a feature that would have given Apple the ability to scan photos on phones without the consent of iPhone owners. A responsible product rollout should have included a risk assessment for scams around their product. Apple should have taken these domains off the market; it is unclear why they failed to do so.
Interestingly, safety-apple.com and kids-apple.com are already owned, but a quick scan of the whois records suggests that they are not owned by Apple.
Imagine a person on the receiving end of an email from the alerts-apple.com domain getting a message that said their images had been flagged for CSAM imagery, and that they needed to go to this web site to dispute the charge. Imagine a targeted ad going to a kid on their phone making the same claim, and pointing them at the images-apple.com domain. This is a disaster waiting to happen.
If I can find six of these domains in under 5 minutes, surely Apple can do better — and rest assured, people who make a living from online crime will fill any void Apple leaves in place.
By leaving junk domains available and on the market, Apple exposes their customers to greater risk. The exact feature Apple claims will protect people creates the conditions that criminals can exploit to target the people Apple claims to want to protect.
4. This is an EdTech Problem
In the edtech world, unfortunately, a lot of companies could see their branding and corporate identity be used in typosquatting attacks. A tool like DNSTwister will pick off some obvious candidates for typosquatting, but some prime candidates for fraudulent domain names use plausible variants that don’t rely on misspellings — such as the examples above, for Apple.
Any edtech service that delivers a mission critical tool for a school should own variants on their domain that include the words “alert-“, “service-“, “admin-“, “maintenance-“, “mail-“, etc.
To provide one of many examples, imagine a targeted email directed at tech staff or other school employees (many of whom are listed on school and district web sites) from “alert-yourLMSname.com” saying that your courses were set to be deleted, and you needed to log in to stop the deletion. Bonus points for sending this email early in the morning, or toward the end of the day on Friday. Remember: in many cases, a successful attack on an organization only needs to succeed with one person.
So, edtech folks (and everyone else) – spend some money on domain names. 100 domains cost 1500.00. That’s a lot of prevention.
When I have discussed typosquatting with edtech people in the past, I have had folks who work in privacy and security — in some cases, at very large and well known companies — state that they don’t need to worry about typosquatting because they secure their emails with DKIM, SPF, and DMARC. And this always blows my mind a little bit, and helps highlight one of the reasons why online security is hard.
To start, as shown in the first example with Twitter, anyone can set up DKIM, SPF, and DMARC on domains they can control. Companies absolutely should do that. It helps prevent email spoofing, and that’s a very good thing. But it does nothing about typosquatting because typosquatting by definition means that the attacker has a domain at their disposal – which means that the attacker can also set up DKIM, SPF, and DMARC, in addition to setting up a web site using the typosquatted domain. And yes, attackers are acquiring infrastructure.
We’ll cover this in more detail in the “Mitigation” section, but if you ask a vendor how they work to mitigate typosquatting and they respond with some version of “We use SPF, DKIM, and DMARC”, thank them for their time and end the conversation because you are speaking with someone who is either intentionally inaccurate or unintentionally uninformed.
5. Cloning Sites is Easy
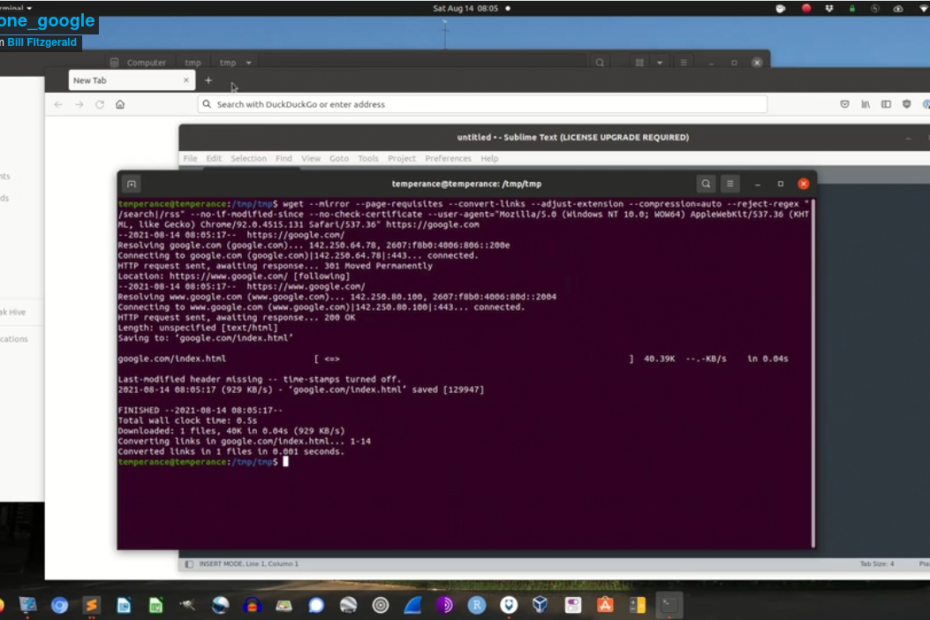
The number of tools available to clone web sites boggles the mind. For copying single pages, you can just use your web browser’s “save as” feature. If you want to use the terminal or bash scripts, you can use wget, as shown in the screencast above. If you want to get more sophisticated, you can use the requests module in python. There is also a fully functional kit to create social engineering attacks which includes the feature of cloning a web site, and multiple guides online describing how to use it.
6. Mitigation
6A. Personal Level
The vast majority of online attacks, including those that leverage typosquatting, require you to click a link or visit a malicious site. A blend of skepticism and verification can help prevent these attacks from being successful.
- Never trust shortened links. There are many link expanders; DuckDuckGo is a solid option: https://duckduckgo.com/?q=expand+bit.ly%2F2iSHN7p
- Check to see if links/domains are malicious: there are a range of online sites that do this; https://www.virustotal.com/gui/home/url and https://www.urlvoid.com are solid.
- Avoid opening links on your phone if it’s a message that you aren’t expecting, especially if the message that elicits an emotional reaction, or when you are rushing. This is true for links received via text, email, iMessage, Signal, etc. If you feel like the message needs immediate attention, call or email the sender with a new message (ie, not by responding to the original text or email). The smaller screens of a phone, in addition to the inability to right click, and the smaller interface to copy a link or quickly switch tabs, can make verification on a phone more time consuming and/or awkward.
- If you are even mildly unsure about who is contacting you, reach out via another channel to verify the communication. If you received a text, connect via email. If you received an email, try and connect by phone.
Mitigating phishing or spearphishing attacks that use typosquatted domains is a mix of technical and psychological responses, and requires changes in behavior to be most effective. Many successful attacks work because they are crafted in a way that elicits an emotional response. This is similar to how misinformation and disinformation are spread. Cultivating skepticism can keep you safer and more informed online.
Finally, if you can afford it, get an external hard drive and back up your files regularly. Your personal backup cadence should be determined by the amount of work you do and store on your computer. If an attack is successful (and realistically, most of us will get compromised at some point) and you have a reliable, current backup, in many cases you can wipe your computer or reset your phone to factory settings and start from scratch. This takes time to set up, and time to maintain, but it’s a lot easier than paying a ransom to get access to your data.
6B. School Staff
The subject of effective or adequate school security is beyond the scope of this post (and if we’re being candid, beyond the understanding of most vendors that sell these services to schools). The mitigation strategies outlined here are narrowly focused on steps that can help mitigate some of the risk from phishing and spearphishing attacks that use typosquatted domains. The focus in this post is on low cost or no cost strategies that generally require behavioral change, rather than new tech or hardware.
Make sure all staff are trained on the personal level techniques discussed above. This includes encouraging staff to reach out to other staff to vet material, and requires top down support from leadership where people are encouraged to verify messages from their colleagues and/or outside vendors.
Avoid gotcha trainings (for example, sending a “fake” email, and then requiring training for any staff who interact with it). They erode trust. Don’t pay money for gotcha trainings. If you have in the past, that’s fine, but moving forward, just stop.
Ask vendors what specific steps they take to mitigate the risk of typosquatting using their domains. Right answers include buying junk domains, listing the domains they control and from where they send emails, and training their staff to support customers. If the vendor says that they do not need to worry about typosquatting or similar attacks because they have DKIM, SPF, or DMARC set up, that is the wrong answer.
Avoid using messaging or announcement services that obfuscate urls. Services like this train people to expect and tolerate junk urls as part of their regular routine, and this is bad practice. SchoolMessenger is a prime example – I have received multiple messages from SchoolMessenger over the years, and in the messages I have received their urls are a mess. Even if the text in the message includes a plain link to https://google.com, their software mangles the email to a long series of strings that begin with “http://track.spe.schoolmessenger.com” – and yes, the initial url is not encrypted, although it’s redirected to an encrypted (https) connection after the link is clicked. The rest of the url includes over 150 alphanumeric characters, including a payload that is base64 encoded and sends along tracking data, including the recipient’s email address. Garbage urls like this get people in the habit of tolerating and clicking on garbage urls, which makes it more difficult for regular people to filter safe content from malicious content.
6C. Vendors
Buy junk domains. This probably the cheapest thing you can do, and it’s drop dead simple, and requires no technical skill.
Train all your support staff in mitigation techniques, and make sure your support staff and sales team can speak intelligently about issues of basic security, and that they have a person in your organization who can help with more comprehensive questions.
Identify the domains you will use for sending emails, and make sure you have SPF, DKIM, and DMARC set up on these domains. This won’t protect against typosquatting, but it will protect against email spoofing.
In any notifications you send, don’t obfuscate or mangle urls. Preserve simple links, and ensure that when a person mouses over links in your messages, they see the correct, accurate url.
7. Closing
Mitigating typosquatting requires layers of defensive practice, and the process of getting junk domains off the market is akin to whackamole. However, vendors have the greatest power to make typosquatting more difficult for criminals, because theoretically vendors have some motivation to ensure that their brand isn’t used as a central component in attacks. In practice, unfortunately, we don’t appear to be seeing vendors taking the relatively inexpensive steps required to pull their junk domains off the market. Perhaps this is because the impacts of successful attacks are only felt by individual customers, and any impact to the vendor is indirect.
While buying every junk domain is not possible, even a superficial search shows a lot of prime candidates are still available. Practically speaking, this means that a criminal ring can get up and running with one thousand junk domains for 15,000.00 US. That initial investment is potentially covered by the first successful attack; everything after that is profit. For the criminals, that math works out.
Vendors: please, buy your junk domains.